1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
| #define INITGUID
#include <windows.h>
#include <evntrace.h>
#include <evntcons.h>
#include <iostream>
#include <iomanip>
#include <dbghelp.h>
#include <unordered_map>
#pragma comment(lib, "dbghelp.lib")
#include <psapi.h>
static const GUID KernelMemoryGuid = { 0xD1D93EF7, 0xE1F2, 0x4F45, { 0x99, 0x43, 0x03, 0xD2, 0x45, 0xFE, 0x6C, 0x00 } };
static const GUID Microsoft_Windows_Threat_Intelligence = { 0xF4E1897C, 0xBB5D, 0x5668, { 0xF1, 0xD8, 0x04, 0x0F, 0x4D, 0x8D, 0xD3, 0x44 } };
std::unordered_map<DWORD, HANDLE> processHandleMap;
bool InitializeSymbolHandlerForProcess(DWORD processId) {
HANDLE hProcess = OpenProcess(PROCESS_QUERY_INFORMATION | PROCESS_VM_READ, FALSE, processId);
if (hProcess == nullptr) {
std::cerr << "Failed to open process " << processId << ". Error: " << GetLastError() << std::endl;
return false;
}
if (!SymInitialize(hProcess, NULL, TRUE)) {
std::cerr << "Failed to initialize symbol handler for process " << processId
<< ". Error: " << GetLastError() << std::endl;
CloseHandle(hProcess);
return false;
}
processHandleMap[processId] = hProcess;
return true;
}
void CleanupSymbolHandlers() {
for (auto& entry : processHandleMap) {
SymCleanup(entry.second);
CloseHandle(entry.second);
}
processHandleMap.clear();
}
std::string ResolveFunctionNameForProcess(HANDLE hProcess, ULONG64 address) {
char buffer[sizeof(SYMBOL_INFO) + MAX_SYM_NAME * sizeof(TCHAR)] = { 0 };
PSYMBOL_INFO symbol = reinterpret_cast<PSYMBOL_INFO>(buffer);
symbol->SizeOfStruct = sizeof(SYMBOL_INFO);
symbol->MaxNameLen = MAX_SYM_NAME;
DWORD64 displacement = 0;
if (SymFromAddr(hProcess, address, &displacement, symbol)) {
return std::string(symbol->Name);
}
else {
return "Unknown";
}
}
ULONG64 lastAddress = 0;
int flag = 0;
VOID WINAPI EventCallback(PEVENT_RECORD EventRecord) {
DWORD processId = EventRecord->EventHeader.ProcessId;
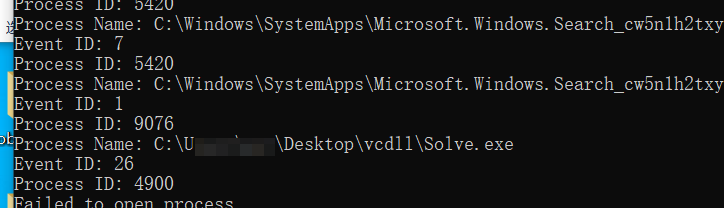
std::cout << "Event ID: " << EventRecord->EventHeader.EventDescriptor.Id << std::endl;
std::cout << "Process ID: " << processId << std::endl;
char processName[MAX_PATH] = { 0 };
HANDLE hProcess = OpenProcess(PROCESS_QUERY_INFORMATION | PROCESS_VM_READ, FALSE, processId);
if (hProcess) {
DWORD length = GetModuleFileNameExA(hProcess, NULL, processName, sizeof(processName));
if (length > 0) {
std::cout << "Process Name: " << processName << std::endl;
}
else {
std::cout << "Failed to get process name." << std::endl;
}
CloseHandle(hProcess);
}
else {
std::cout << "Failed to open process." << std::endl;
}
}
ULONG WINAPI BufferCallback(PEVENT_TRACE_LOGFILE Buffer)
{
return TRUE;
}
int main() {
system("pause");
__debugbreak();
TRACEHANDLE sessionHandle = 0;
TRACEHANDLE traceHandle = 0;
EVENT_TRACE_PROPERTIES* traceProperties = (EVENT_TRACE_PROPERTIES*)malloc(sizeof(EVENT_TRACE_PROPERTIES) + 1024);
if (!traceProperties) {
std::cerr << "Failed to allocate memory for EVENT_TRACE_PROPERTIES." << std::endl;
system("pause");
return 1;
}
ZeroMemory(traceProperties, sizeof(EVENT_TRACE_PROPERTIES) + 1024);
traceProperties->Wnode.BufferSize = sizeof(EVENT_TRACE_PROPERTIES) + 1024;
traceProperties->Wnode.Guid = Microsoft_Windows_Threat_Intelligence;
traceProperties->Wnode.Flags = WNODE_FLAG_TRACED_GUID;
traceProperties->LogFileMode = EVENT_TRACE_REAL_TIME_MODE;
traceProperties->MaximumFileSize = 0;
traceProperties->LoggerNameOffset = sizeof(EVENT_TRACE_PROPERTIES);
WCHAR sessionName[] = L"MyKernelMemorySession";
ULONG status = StartTrace(&sessionHandle, sessionName, traceProperties);
if (status != ERROR_SUCCESS) {
std::cerr << "Failed to start ETW session. Error: " << status << std::endl;
free(traceProperties);
system("pause");
return 1;
}
ENABLE_TRACE_PARAMETERS enableParameters = { 0 };
enableParameters.Version = ENABLE_TRACE_PARAMETERS_VERSION;
enableParameters.EnableProperty = EVENT_ENABLE_PROPERTY_STACK_TRACE;
status = EnableTraceEx2(
sessionHandle,
&Microsoft_Windows_Threat_Intelligence,
EVENT_CONTROL_CODE_ENABLE_PROVIDER,
TRACE_LEVEL_INFORMATION,
0x8000000000000040,
0,
0,
NULL
);
if (status != ERROR_SUCCESS)
{
system("pause");
std::cerr << "Failed to enable ETW provider. Error: " << status << std::endl;
StopTrace(sessionHandle, sessionName, traceProperties);
free(traceProperties);
system("pause");
return 1;
}
EVENT_TRACE_LOGFILE logFile = { 0 };
logFile.LoggerName = sessionName;
logFile.ProcessTraceMode = PROCESS_TRACE_MODE_EVENT_RECORD | PROCESS_TRACE_MODE_REAL_TIME;
logFile.EventRecordCallback = (PEVENT_RECORD_CALLBACK)(EventCallback);
logFile.BufferCallback = BufferCallback;
traceHandle = OpenTrace(&logFile);
if (traceHandle == INVALID_PROCESSTRACE_HANDLE) {
system("pause");
std::cerr << "Failed to open trace. Error: " << GetLastError() << std::endl;
StopTrace(sessionHandle, sessionName, traceProperties);
free(traceProperties);
system("pause");
return 1;
}
std::cout << "Listening for ETW events. Press Ctrl+C to stop..." << std::endl;
status = ProcessTrace(&traceHandle, 1, NULL, NULL);
if (status != ERROR_SUCCESS) {
system("pause");
std::cerr << "Failed to process trace. Error: " << status << std::endl;
}
CloseTrace(traceHandle);
StopTrace(sessionHandle, sessionName, traceProperties);
free(traceProperties);
system("pause");
std::cout << "ETW session stopped." << std::endl;
system("pause");
return 0;
}
|